How to secure Azure storage account with a CDN
You have an Azure storage account and you want to have a public endpoint to share with third party.
In this situation, the easiest way is to let your storage account public visible, but of course this is NOT secure. What i want to explain with this article is how to be ready to share your storage account endpoint publicly but in a secure way.
This articles applies to both situation, with some differences explained above, if you have a Static content hosted on the Azure static website (on the storage account) or within a blob container.
First of all, i would to give the solution: we will use the Azure CDN in front to have protect our assets, let the solution be scalable, geo-distributed, quick in response using the cache feature and protect by DDOS attack.
If you don't know what is an Azure CDN you can check the official documentation here and its features here.
To improve the security, i also suggest to put a WAF in front (you can use a 3rd party WAF or an azure WAF).
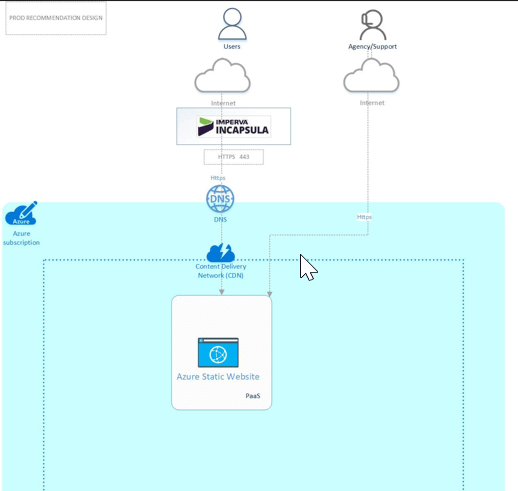
The reference architecture we will follow is explained on this picture:
Now let's see how to setup the following on Azure and which kind of configuration i suggest.
To avoid the people to connect to the static website directly without connect to the WAF and to the CDN, the main configuration is to restrict the access using the Storage account Firewall with the Azure CDN ips. The Azure CDN with the custom rules based on the invoker ips not equal a list of the know WAF ips [this is optional] and use the cdn endpoint as origin of the WAF configuration.
All those configurations can be done using azure cli and via portal.
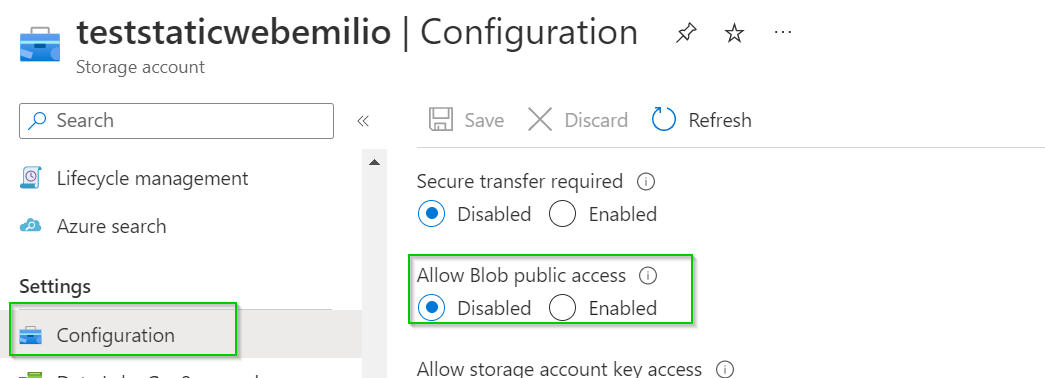
The first configuration is on the Storage account, disable "allow blob public access" on the configuration panel. This is need only if you are considering the Static Website. Check "Image 2"
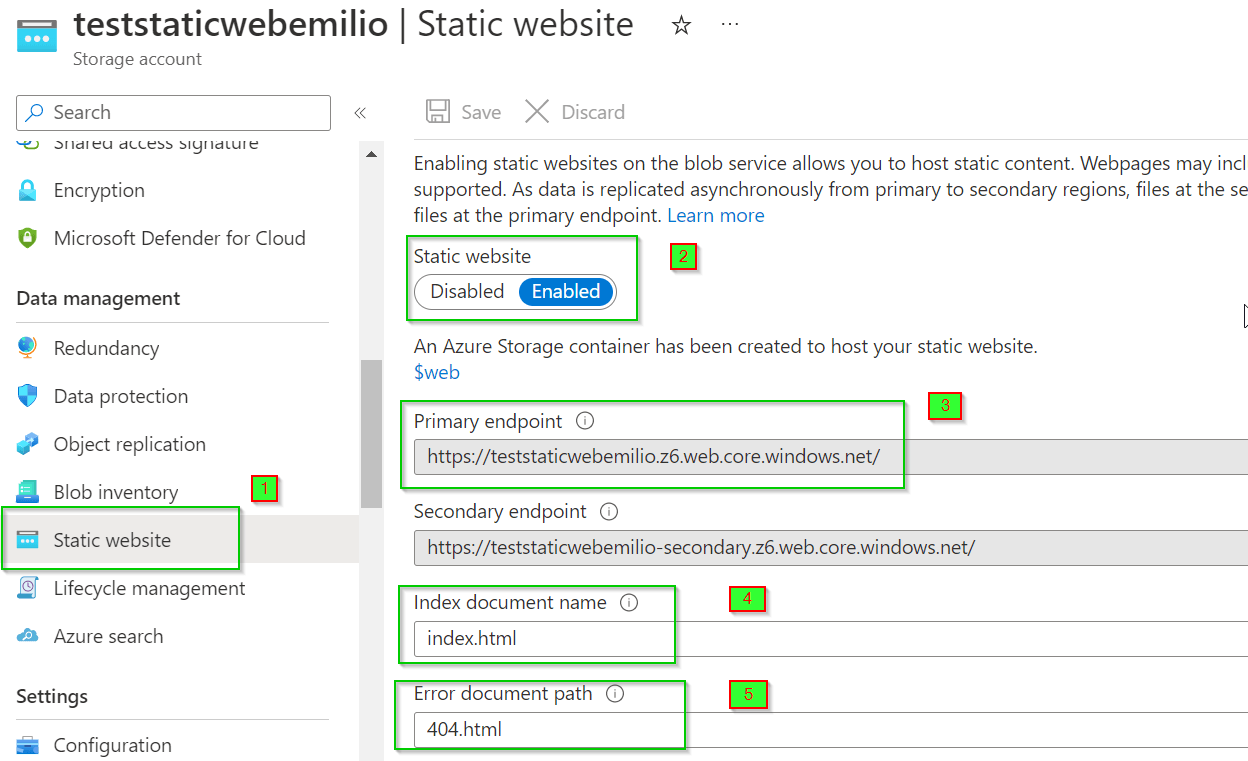
Then enable the static website configuration, check "Image 3". The configuration include the initial file to show when you invoke the basic url (in my case is index.html) and the default error page (in my case 404.html). Those file need to be uploaded on the related blob.
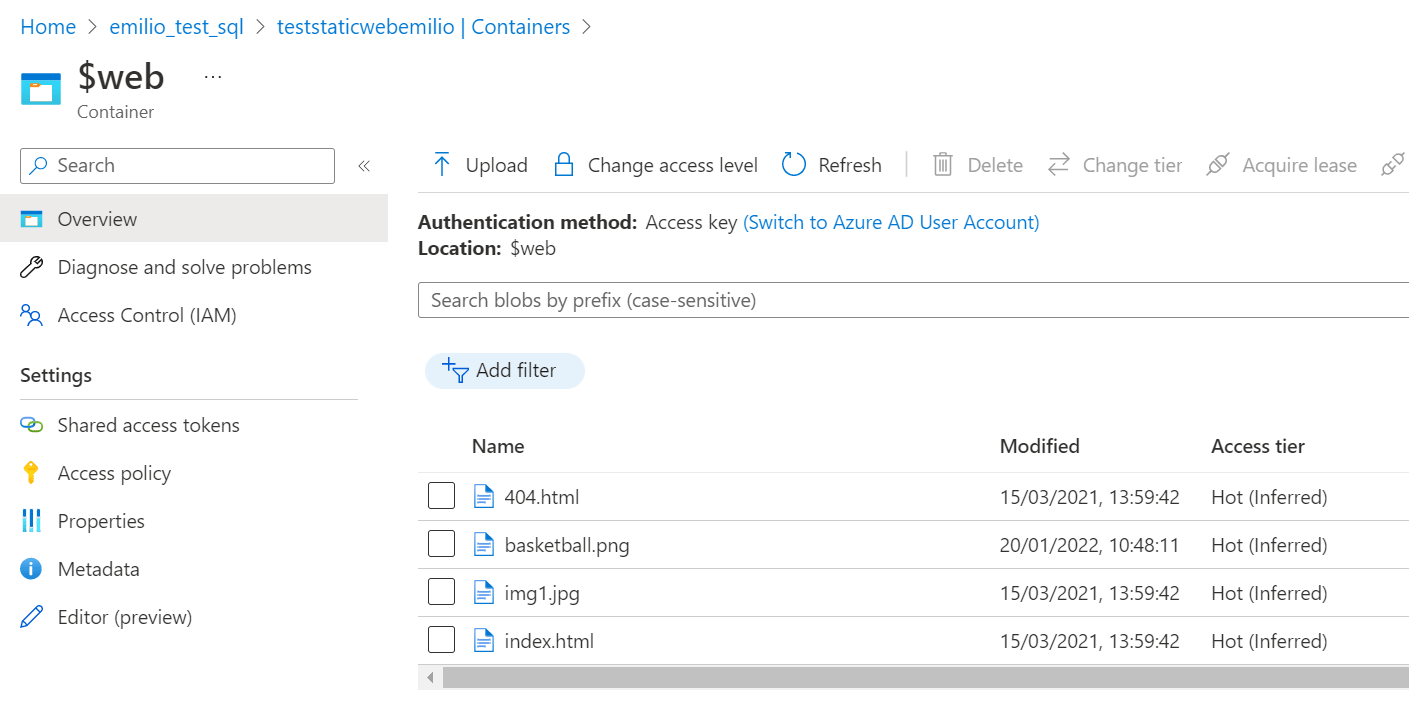
When you enable the static website, Microsoft will create a specific Blob container called $web where you have to upload files you want to show with static website url. Check "Image 4".
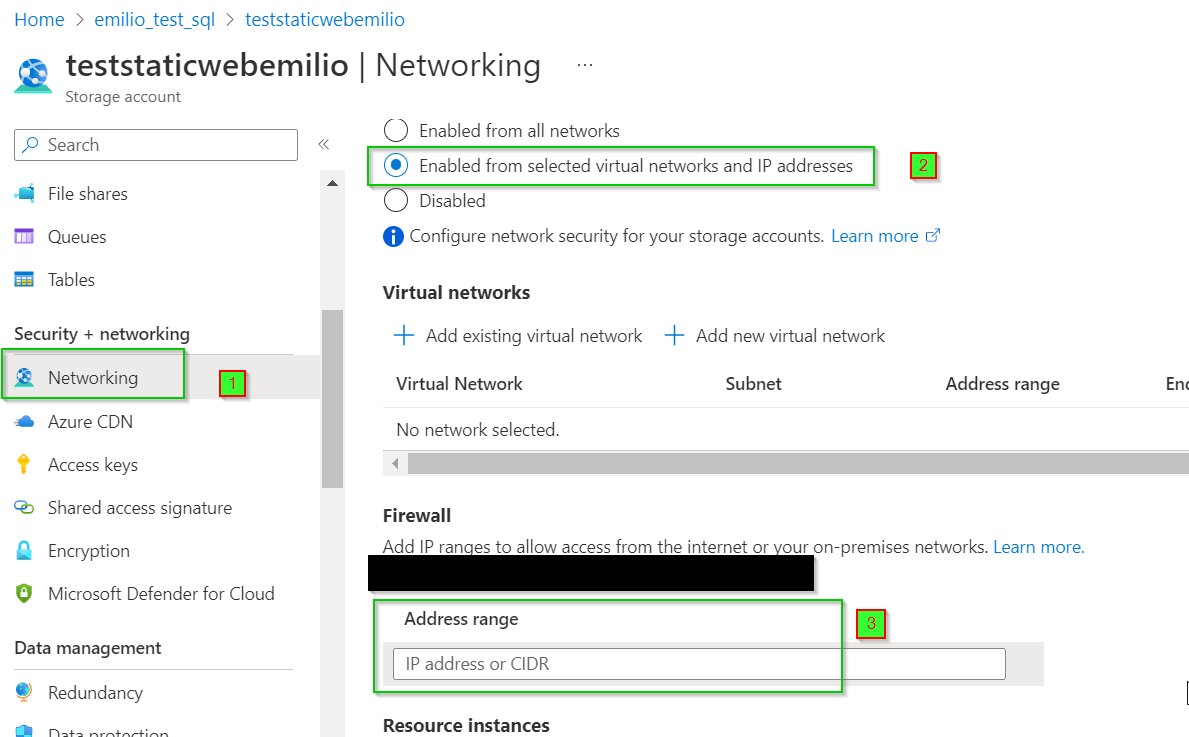
Now let's finalize the configuration on the storage account, enabling the firewall and adding all the ips of the microsoft CDN.
Since microsoft merged front door and azure cdn resoruce, the list of the ips to whitelist is present can be downloaded directly on Microsoft website here: Download Azure IP Ranges and Service Tags – Public Cloud from Official Microsoft Download Center
The tag to get is "Frontdoor backend" and you need to put this list on the Firewall of the storage account, field 3 of "Image 5"
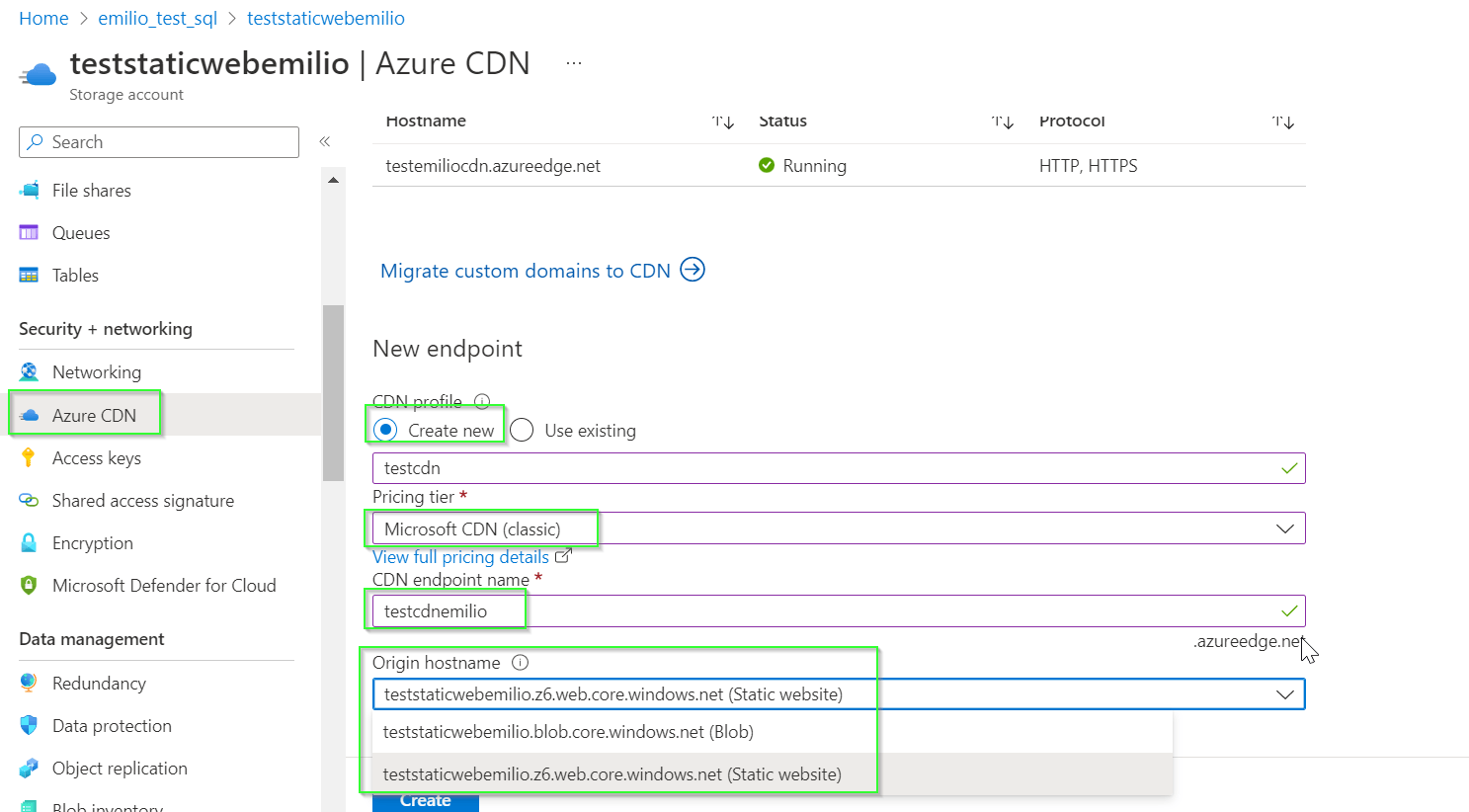
Now finally the last part of the configuration, adding the CDN. The cdn can be add as "new resoruce" or just enabling it on the storage account configuration under "azure cdn". The result is the same, a new cdn endpoint resource. Be sure to select Azure CDN, the correct origin (Static website, as for our example, or blob). Check "Image 6"
Ok, now we are ready to test our configuration.
Please bear in mind, when you use the Static Website feature, each file need to be linked separately, you cannot browse the files if you don't use the portal, going on the blob container $web.
If you are configuring the blob and not the static website, please remember to add the sas token to the URL to invoke file endpoint.
The CDN allow you to add some other rules to secure the access to the CDN endpoint, for example create a rule to add a specific list of IPs - if you want to add the WAF in front or some other rules.
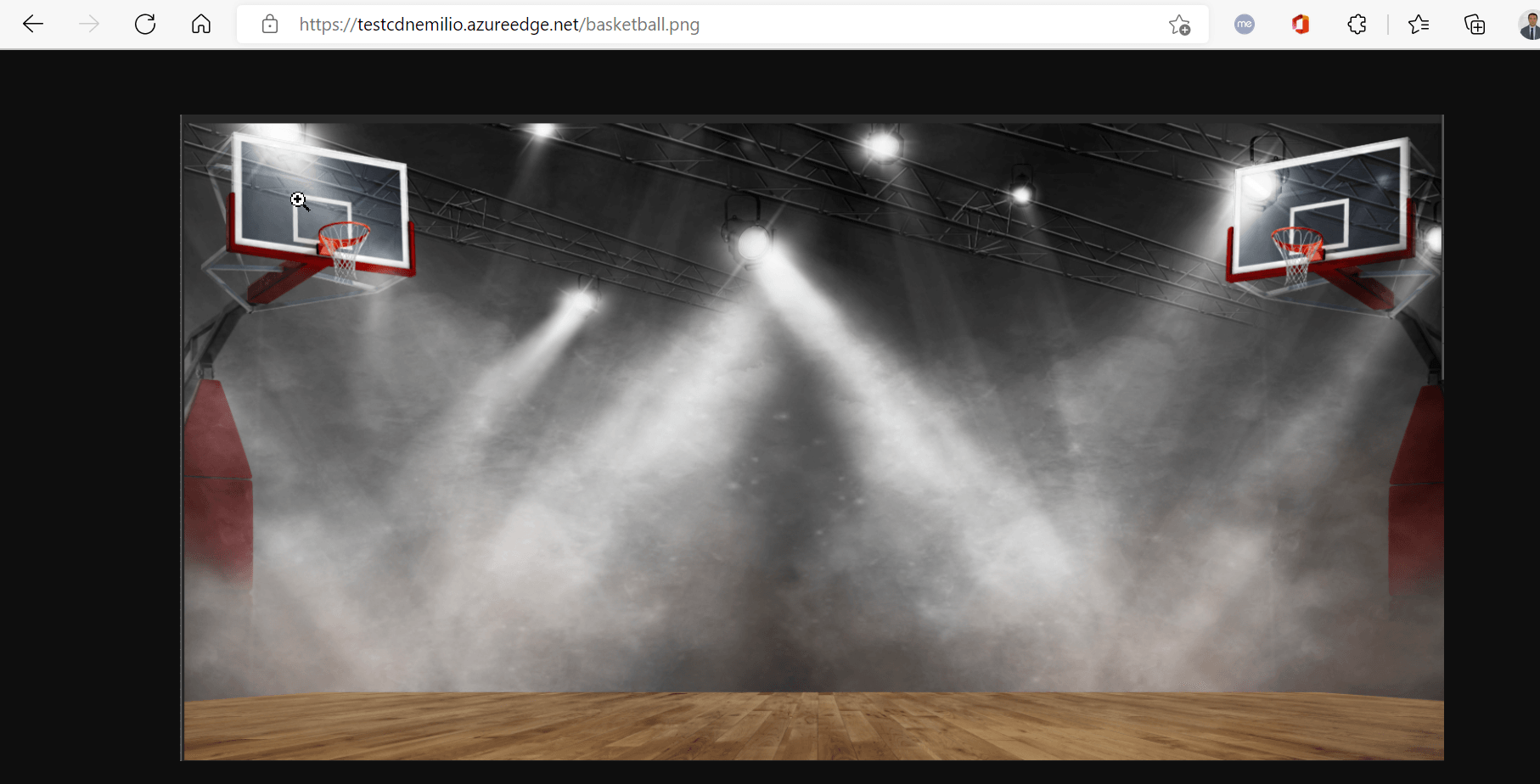
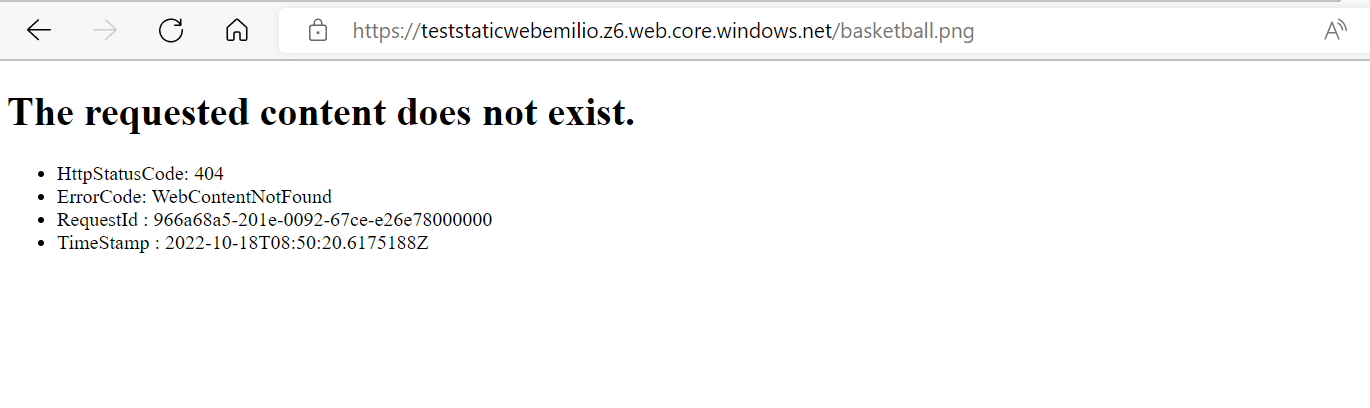
If all the configurations have been done correctly you can access correctly to a specific file within the cdn url (Image 7) and not directly within the storage account endpoint (Image 8).